As a Managed Security Service Provider (MSSP) that specialises in helping DoD contractors navigate the complexities of cybersecurity and compliance, we’ve been closely monitoring the evolution of the Cybersecurity Maturity Model Certification (CMMC) since its inception in 2020 and going back to 2016 when DFARS 7012 was just getting off the ground.
On November 4th, 2021, the DoD released CMMC 2.0 which includes several updates and changes to the original framework.
This short guide was written for DoD contractors so that they can understand what these changes mean for their organizations and take the appropriate actions for their company.
Summary of Key Updates: CMMC 1.0 vs. CMMC 2.0
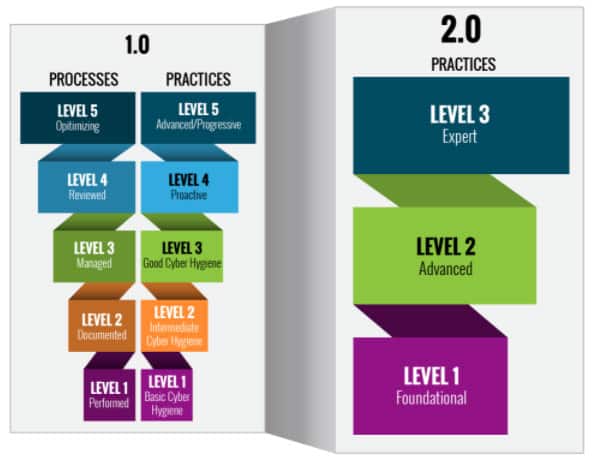
- Only 3 CMMC Levels: CMMC Levels 2 and 4 from the original CMMC framework have been eliminated, leaving only 3 current CMMC Levels. These Levels are detailed below.
- Level 1: Now only requires an annual self-assessment and affirmation by company leadership. No changes to the 17 basic cyber hygiene practices required.
- Level 2: The “old” CMMC Level 3 now becomes Level 2. 20 controls have been eliminated from the original framework’s Level 3 requirements, leaving contractors only having to implement the 110 controls from NIST 800-171. The DoD will identify “prioritized acquisitions” that must undergo an independent third-party assessment against the new Level 2 requirements. All other organizations will only need to perform a self-assessment and affirmation by company leadership.
- Level 3: This level will replace CMMC Levels 4 and 5 from the original framework. While details are still being worked out, it is expected that this level will include controls from NIST SP 800-172 and assessments will be government-led.
Visualizing the New CMMC 2.0 Levels:
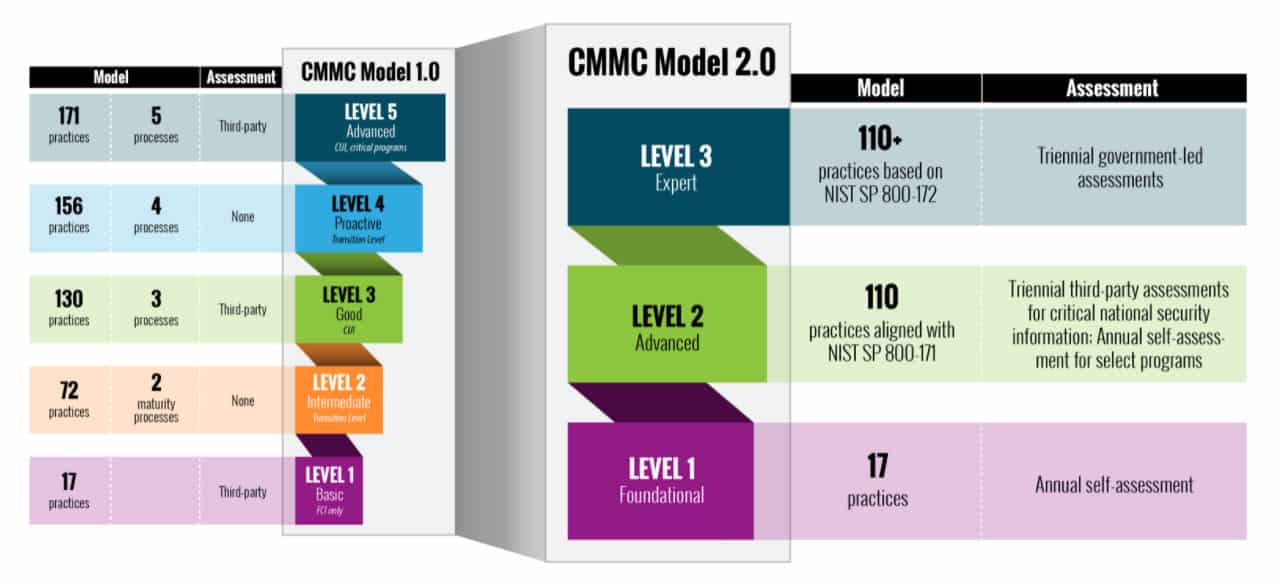
Source: https://www.acq.osd.mil/cmmc/about-us.html
CMMC 2.0 Changes Explained
Beyond the modification of the Levels, here are two key changes that DoD contractors need to be aware of.
Change One: Assessment Requirements
Level 1: Self-Assessments
One of the biggest complaints from DoD contractors was that CMMC 1.0 required them to undergo third-party certification, even at CMMC Level 1. CMMC 2.0 eliminates this requirement. Instead, contractors can perform their own self-assessments and will only be required to affirm annually that they comply with CMMC 2.0 Level 1.
Level 2: Third-Party Assessments & Self Assessments
CMMC Level 2 is divided into two separate assessment requirements. Only DoD Contractors working on “prioritized acquisitions” will need to undergo a third-party assessment every 3 years. All other contractors are permitted to perform a self-assessment and affirm annually that they comply with CMMC 2.0 Level 2.
The DOD has not yet announced how it will prioritize acquisitions.
Level 3: Government-Led Assessments
CMMC Level 3 applies to only the most sensitive and high-risk DoD projects. Therefore DoD contractors who fall into this category will need to undergo a government-led assessment every 3 years.
Change Two: Allows Plan of Action and Milestones (POA&M)
Another big criticism from DoD Contractors was that they were being required to meet every single practice and process for their required Level of certification. CMMC 2.0 allows for the DoD contractors to submit a Plan of Action and Milestones, also known as a POA&M, for those practices and processes not yet met.
Important: DFARS 7012, 7019 & 7020 Are Still Required
A very important fact is that DFARS 7012, 7019 and 7020 are still required for DOD contractors who handle controlled unclassified information, or CUI. To comply with these requires the implementation of NIST 800-171 which equates to CMMC Level 2 – Advanced.
Final Thoughts & Next Steps
The bottom line is that CMMC 2.0 significantly streamlines the requirements and eliminates many of the barriers to compliance, especially for smaller DoD contractors with less resources to dedicate to cybersecurity compliance.
We continue to strongly advise that companies do not sit on the sidelines and continue to explore their options for meeting their required Level of CMMC compliance. We heed this advice because of the following reasons:
- DFARS 7012, 7019 and 7020 are still required for DoD contractors Handling CUI.
- Early adopters of NIST 800-171 are likely to have a market advantage with their DoD customers and partners.
- DoD contractors should consider the risks to their organizations and balance sheets from ransomware and other types of breaches that NIST 800-171 can defend against.
We understand that many DoD contractors lack the resources in-house to complete their own self-assessments. That’s why many contractors choose to outsource the task to a provider like SysArc. We can take the burden of compliance off your team’s plate while at the same time protecting your IT infrastructure against cyber criminals.
If you have questions about implementing any of the cybersecurity controls in CMMC and about how SysArc can help, feel free to give us a call. We’ll be happy to speak with you and help you find a solution that works best for your business.